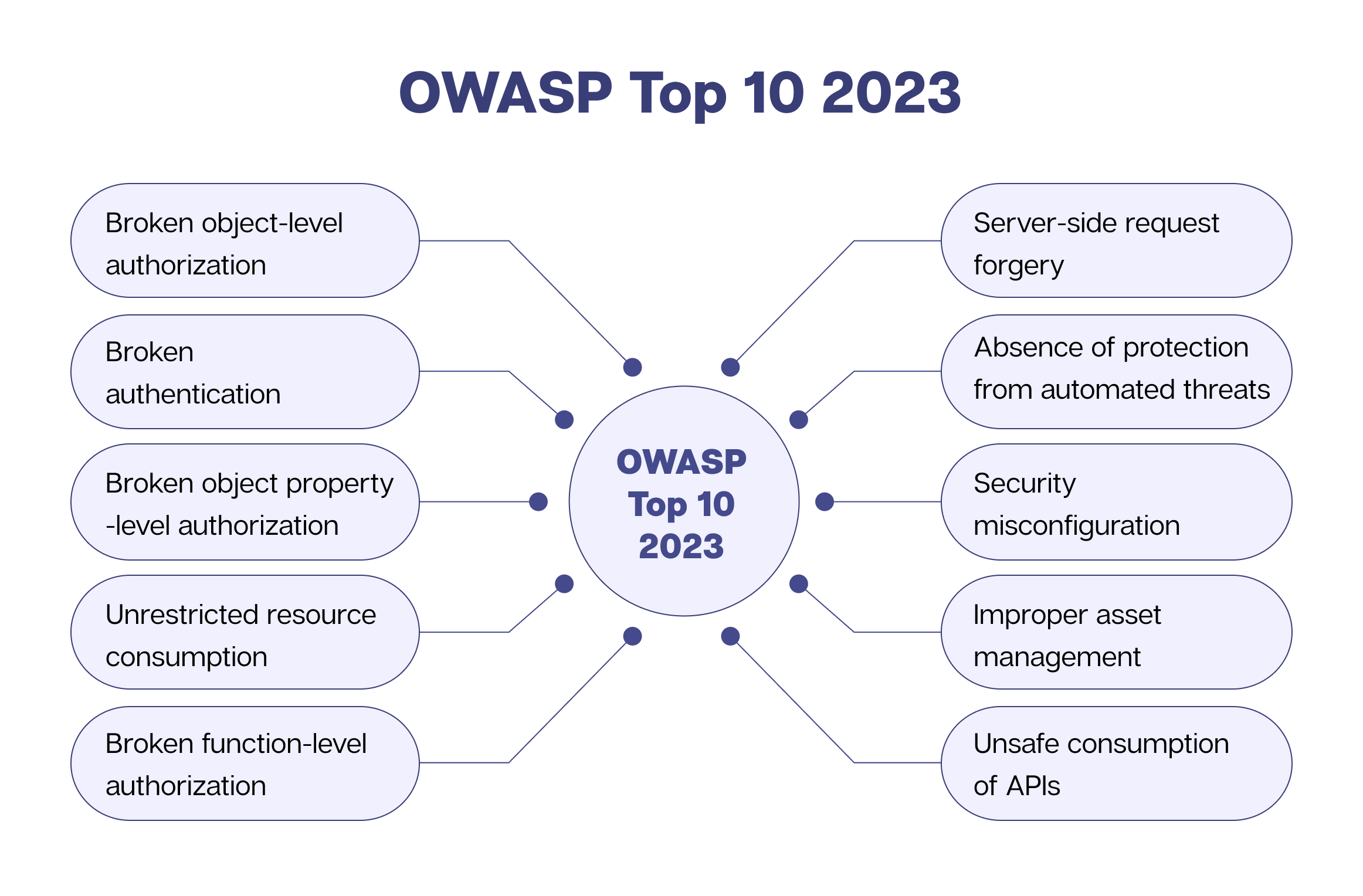
2. Broken authentication
Broken authentication is critical to ensure application security as it validates users’ identities before allowing them to access a protected resource. This is like a security gateway for any application. So, keeping a tab on a user’s identity, authentication, password security management, and session management is essential.
With the introduction of two-factor authentication (2FA) and other stricter authentication measures, broken authentication issues have come down, but they are still significant.
3. Broken object property-level authorization
Broken object property-level authorization occurs when an application programming interface (API) provides authorization to data objects based on the role of the users but fails to ascertain if the user is allowed to access those specific data entities.
It focuses on the security of a system’s access control configuration and its power to limit liberties at the object property level.
The immediate impact of these exposures is attackers have unauthorized access to sensitive data. It is a common issue because the server component depends more on external parameters.
4. Unrestricted resource consumption
The unrestricted resource consumption is a continually overlooked API vulnerability. API requests consume CPU, memory, network, and storage resources. This attack can be carried out by transmitting multiple requests to the target system.
This OWASP vulnerability ensues when an application fails to specify the consumption of resources, such as CPU cycles, memory, or network bandwidth.
Unrestricted resource consumption makes the targeted system unstable or unavailable, which can have severe outcomes for the business or organization that depends on the system. It can result in denial-of-service (DoS) attacks and other malicious exercises.
5. Broken function-level authorization
The broken function-level authorization susceptibilities encourage unauthorized users to access certain functions, features, and privileges they should otherwise not have access to.
Once the attackers access unauthorized resources, they exploit broken function-level authorization susceptibilities to create/delete accounts, take over another user’s account, and escalate privileges to gain administrative access.
This OWASP Top 10 API security vulnerability mainly occurs due to inadequate authorization checks, input validation, and weak access controls.
6. Server-side request forgery
SSRF or Server-Side Request Forgery events occur due to a distant resource’s lack of URL validation. Malicious actors often send requests to servers from unknown locations, bypassing VPN or firewall protection.
Hackers can successfully do this by manipulating URLs. They can achieve this goal by replacing the existing URL with a new one. They can also tamper the URL through the URL path traversal technique.
7. Absence of protection from automated threats
As automation technologies such as bots become more challenging to detect and safeguard against, the threat of malicious cyber attacks, such as brute-force attacks, distributed denial-of-service (DDoS) attacks, and credential stuffing attacks, proliferate.
The APIs may not have inherent bugs or flaws, but the underlying business flow is susceptible to excessive activity. Hackers quickly comprehend the API models and business flows to exploit them to their advantage using automated tools eventually.
Such automated attacks can have serious consequences, including security issues without adequate protection, system downtime, data breaches, and financial losses.
8. Security misconfiguration
Not implementing security configuration settings properly leaves applications vulnerable to cyber threats.
Misconfigurations often arise from various sources, including
● Weak passwords,
● Inappropriately configured databases and cloud applications,
● Misconfigured firewalls or network settings, and
● Outdated firmware, leading to data theft, denial-of-service-cyberattacks, and malware attacks.
9. Improper asset management
Using improper inventory/asset management, such as outdated application components, can compromise an entire application’s security.
That is why developers should know the versions of components used in the system and regularly perform security audits to detect potential vulnerabilities and keep them at bay.
10. Unsafe consumption of APIs
APIs are a treasure trove for hackers because they are a doorway to valuable information.
While APIs deliver tremendous benefits, such as quicker development time and improved agility, they pose new security risks if not adequately addressed. In a typical attack scenario, a threat actor manipulates a third-party API.
The attacker determines a third-party API that is weak and exploits it. The not-so-safe consumption of APIs can cause malicious code execution, data leakage, and escalation attacks.
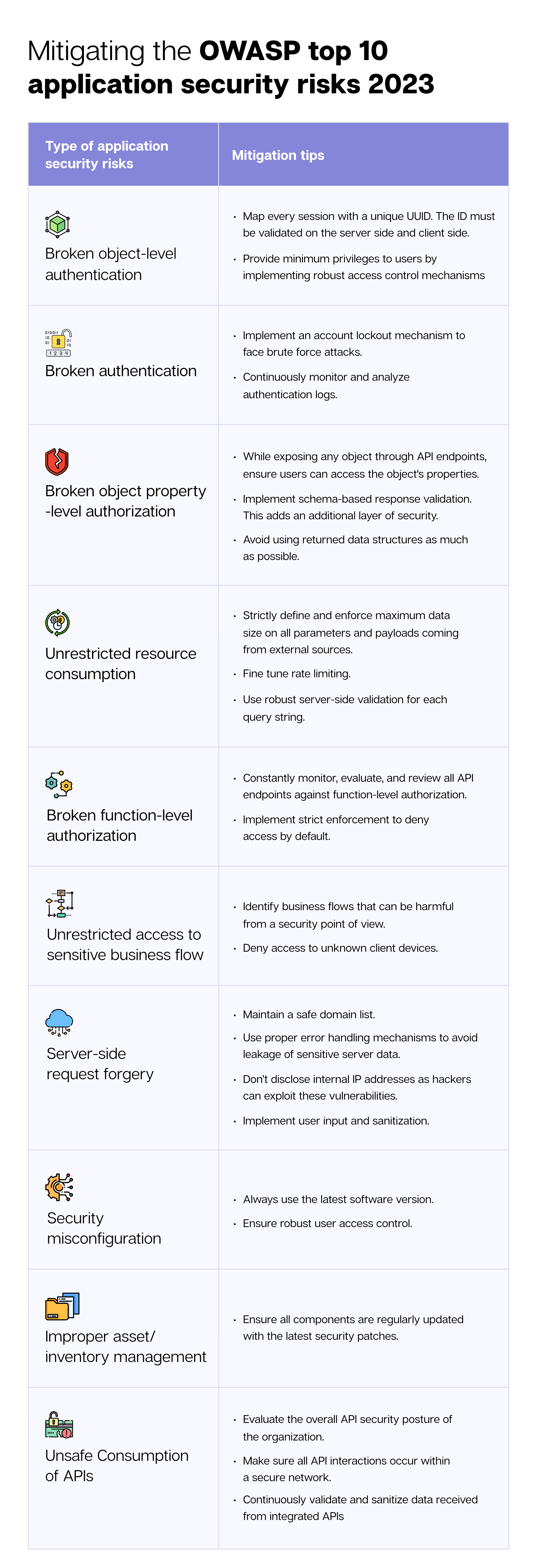
Mitigating the OWASP Top 10 application security risks 2023
Following these actionable tips can help in mitigating the OWASP security vulnerabilities:
What changed in OWASP 2023?
Let’s look at what’s new in the latest OWASP 2023 for a comparative analysis between the OWASP API Top 10 2021 and 2023.
Here is a graphical representation to help you understand the new internal and external vulnerabilities that made entries in the list and what remained unchanged. 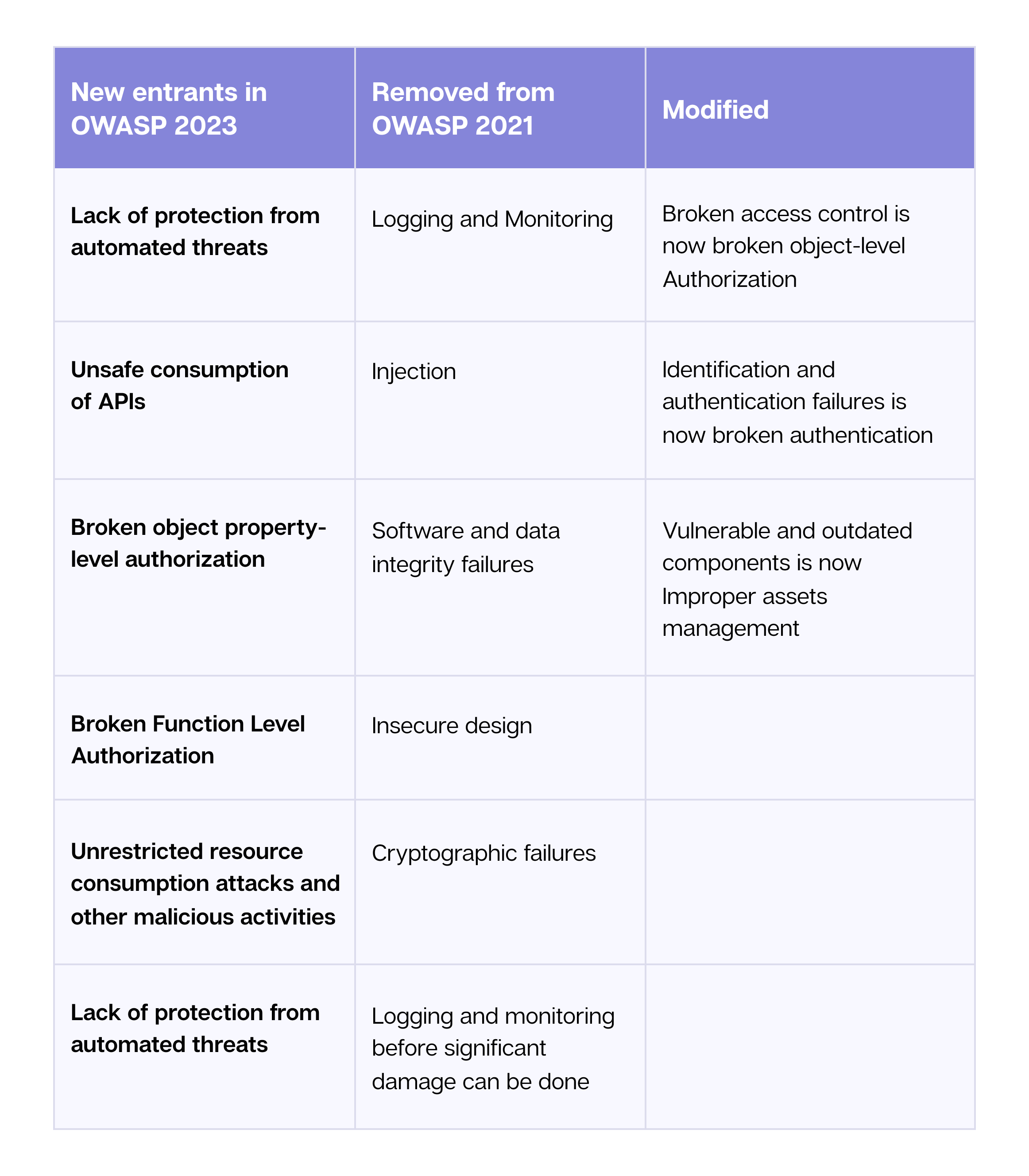
OWASP Top 10 compliance best practices
Below are some of the recommended best practices to stay OWASP compliant:
Familiarize with OWASP Top 10
Familiarizing yourself with the risks is the most effective way to stay OWASP compliant. OWASP Top 10 application security risks 2023 does a fantastic job of creating a valuable repository of the latest security risks and assisting developers in staying informed of various types of application security risks and best practices for application security.
Implement DevSec practices
Most web security risks start with ignoring the basic security aspects. Most developers view adhering to security standards as an unnecessary burden as they fail to realize the long-term implications of ignoring security protocols while coding.
Ensure your tech team implements the best DevSec practices.
Conduct regular security audits
The cybersecurity risk landscape is not static – new risks are continuously evolving. Regular security audits and vulnerability scanning should be part of your organizational culture.
For this, run a good-quality vulnerability scanner to identify and fix common OWASP vulnerabilities.
How Appknox helps
Though the OWASP list offers a good starting point for security teams, manually identifying the gap in the application’s security environment is challenging and time-consuming.
Appknox is a binary-based automated vulnerability assessment tool to quickly identify and track security gaps. After scanning your application, Appknox generates a detailed CVSS report containing potential vulnerabilities mentioned in the OWASP Top 10 list, along with actionable remediation notes.
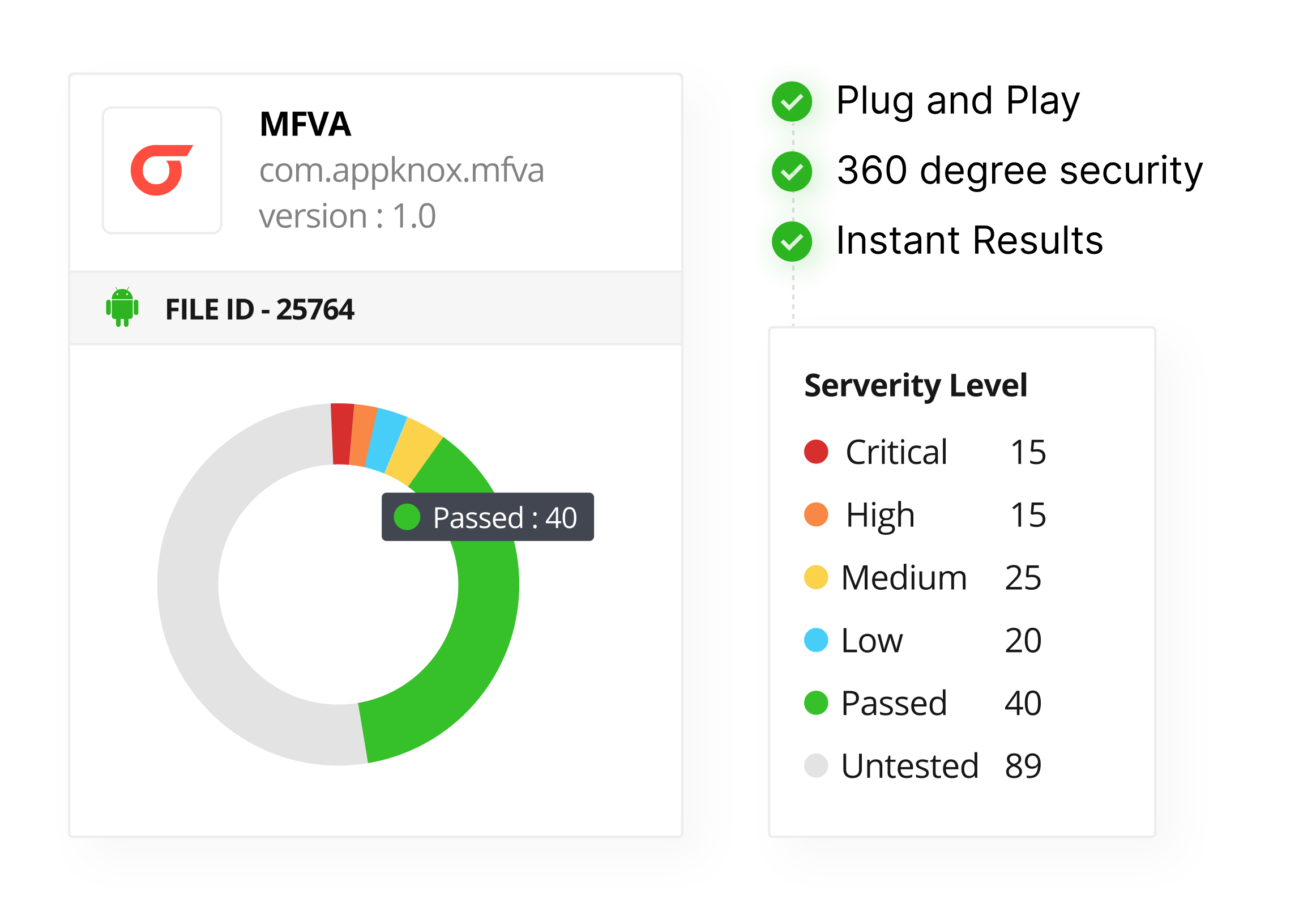
This enables your security teams to understand the risks and fix them promptly. Thus, at Appknox, we ensure your app meets the highest security standards.
Start your free Appknox trial
Frequently Asked Questions (FAQs)
#1. What are the implications of non-compliance with OWASP Top 10?
Though OWASP guidelines are optional, unlike HIPAA, GDPR, and other data standards, the document serves as a benchmark for security professionals worldwide. Non-compliance with these guidelines will lead to data breaches, financial losses, hefty fines, and loss of reputation.
#2. How can I assess my application’s compliance with OWASP 2023?
Assessing OWASP application compliance is a complex task requiring an in-depth assessment of vulnerabilities. Using penetration testing and vulnerability assessment tools provides a 360-degree view of security risks.
These tools can identify risks that may be overlooked during manual security assessment. Some application security testing tools provide a score after a detailed assessment of security scenarios.
#3. How can I improve the application’s compliance with OWASP 2023?
OWASP compliance demands a multipronged approach to evaluate the overall security posture and implement security controls and secure coding practices.
#4. How can Appknox detect potential vulnerabilities before they become significant issues?
Appknox can identify potential weaknesses in application security and proactively detect them before they escalate into significant security issues. This helps to prevent potential security breaches and data leaks.












.png?width=2324&height=1392&name=image%2002%20(1).png)









Discussion about this post