The European Parliament website was knocked offline for several hours on Wednesday by a distributed denial-of-service (DDoS) attack that started shortly after the governing body voted to declare the Russian government a state sponsor of terrorism.
European Parliament President Roberta Metsola confirmed the attack on Wednesday afternoon European time, while the site was still down. “A pro-Kremlin group has claimed responsibility,” she wrote on Twitter. “Our IT experts are pushing back against it & protecting our systems. This, after we proclaimed Russia as a State-sponsor of terrorism.”
While this post was being reported and written, the website became available again and appeared to work normally.
The pro-Kremlin group Metsola referred to is likely the one known as Killnet, which emerged at the start of Russia’s invasion of Ukraine and has posted claims of DDoS attacks in countries supporting the smaller nation. Targets have included police departments, airports, and governments in Lithuania, Germany, Italy, Romania, Norway, and the United States.
Shortly after Wednesday’s attack against the European Parliament started, Killnet members took to a private channel on Telegram to post screenshots showing the European Parliament website was unavailable in 23 countries. Text accompanying the images made a homophobic remark directed at the legislative body.
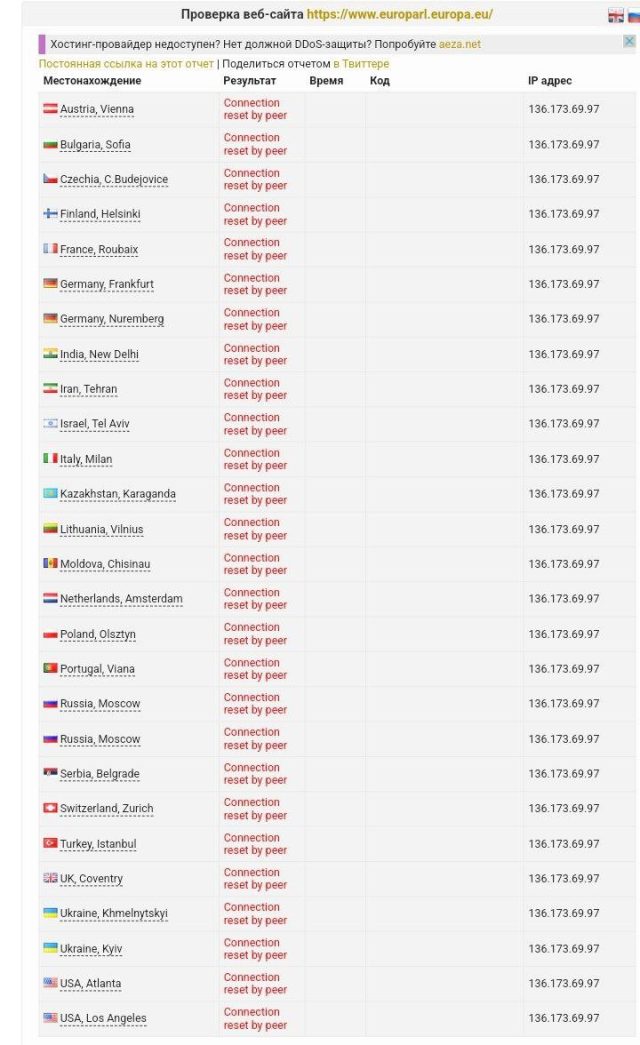
The outage occurred shortly after the parliament overwhelmingly voted to declare the Kremlin a sponsor of terrorism.
Members of the European Parliament “highlight that the deliberate attacks and atrocities committed by Russian forces and their proxies against civilians in Ukraine, the destruction of civilian infrastructure and other serious violations of international and humanitarian law amount to acts of terror and constitute war crimes,” the declaration stated. “In light of this, they recognize Russia as a state sponsor of terrorism and as a state that ‘uses means of terrorism.’”
The resolution was adopted with 494 votes in favor, and 58 against. There were 44 abstentions.
DDoS attacks typically harness the bandwidth of hundreds, thousands, and in some cases, millions of computers infected with malware. After coming into their control, the attackers cause them to bombard a target site with more traffic than they can accommodate, forcing them to deny service to legitimate users. Traditionally, DDoS has been among the crudest forms of attack because it relies on brute force to silence its targets.
Over the years, DDoSes have become more advanced. In some cases, the attackers can increase the bandwidth by as much as a thousand-fold using amplification methods, which send data to a misconfigured third-party site, which then returns a much larger amount of traffic to the target.
Another innovation has been designing attacks that exhaust the computing resources of a server. Rather than clogging the pipe between the website and the would-be visitors—the way more traditional volumetric DDoSes work—packet-per-second attacks send specifc types of compute-intensive requests to a target in an attempt to bring the hardware connected to the pipe to a standstill.
Metsola said the DDoS attacks on the European Parliament were “sophisticated,” a word that’s often misused to describe DDoSes and hacks. She provided no details to corroborate that assessment.




















Discussion about this post